Staff Member
Diamond Supporter
Platinum Supporter
Bronze Supporter
- Messages
- 12,537
- Reactions
- 18,008
You should always be careful opening email attachments, but I wanted to remind everyone today. As of this morning, I've received three emails that look legitimate but certainly were not. Improperly configured email and DNS servers can allow malicious people to 'spoof' email addresses, making it appear an email came from somewhere it didn't. If you do not know the sender, don't open the attachment. If you do know the sender, it's not a bad idea to contact them (even emailing them back is fine) and make sure they meant to send it to you.
Yesterday a severe Linux exploit named Ghost was revealed, and it took quite some time for the release of a patch. I'm not sure if this is related, but if it is, we may see more of this in the coming days.
Anyway, back to the example
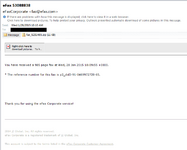
Check this out - everything looks correct, including the 'From' address. Note the zip file attached.

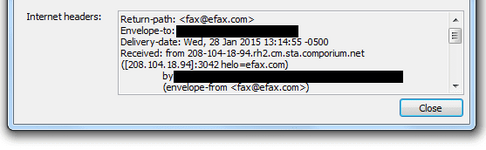
Taking a closer look at the headers reveals that it actually came from what appears to be a dynamic comporium.net mail server, definitely not efax.

I'm not sure what would have happened had I opened this, but I definitely do not want to find out!
Stay safe everyone.
Yesterday a severe Linux exploit named Ghost was revealed, and it took quite some time for the release of a patch. I'm not sure if this is related, but if it is, we may see more of this in the coming days.
Anyway, back to the example
Check this out - everything looks correct, including the 'From' address. Note the zip file attached.
Taking a closer look at the headers reveals that it actually came from what appears to be a dynamic comporium.net mail server, definitely not efax.
I'm not sure what would have happened had I opened this, but I definitely do not want to find out!
Stay safe everyone.











